FREQUENTLY-ASKED QUESTIONS
Didn't find your problem (or a solution) here? Feel free to contact us at by phone at (513) 636-2801, or send an email to dnacore@cchmc.org.
If you decide to email, make sure you include:
- a clear description of your problem, including what you already tried
- any error message(s) you received, copy-pasted verbatim; screenshots are OK, too
Downloading results
What does the rclone error message ssh: handshake failed mean?
When using rclone to download sequencing results, you may see an error message like this:
$ rclone ls --sftp-user=XXXXXXX gsf:
Enter SFTP password:
2025/01/21 10:39:37 Failed to create file system for "gsf:": NewFs: couldn't connect SSH: ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remainYou'll get this error message from rclone if you mis-type your SFTP credentials,
or if those credentials have expired. If the credentials are still within the validity
period (30 days, as of this writing), double-check that you've used the correct username and
password first; failing that,
contact dnacore@cchmc.org
for further guidance.
What does the sftp error message no matching key exchange method found mean?
The SFTP server product that we use (ActiveMFT) offers up older, weaker cryptography protocols during the connection process, which newer SFTP clients may be configured to refuse by default. A future update to ActiveMFT will likely address this problem.
If you are using the command-line sftp client, you can deliberately allow a less
secure algorithm during the key exchange process with the -oKexAlgorithms option:
sftp -P 51022 -oKexAlgorithms=+diffie-hellman-group1-sha1 \
<username>@activemft.research.cchmc.orgUsing a text editor like
nano,
add these lines to your ~/.ssh/config to make this option the
default every time you connect with the ActiveMFT server:
Host activemft.research.cchmc.org
KexAlgorithms +diffie-hellman-group1-sha1Technical details may be found here.
What does the sftp error message WARNING: REMOTE HOST
IDENTIFICATION HAS CHANGED! mean?
If you have not connected to the ActiveMFT SFTP server since December 2024, this message is expected. If you receive this message under any other circumstances, you should contact dnacore@cchmc.org for further guidance.
The cryptographic keys that identify the ActiveMFT server to SFTP clients were intentionally changed in December 2024. SFTP clients typically store "fingerprints" for these keys after the first time you connect, so that you aren't prompted to verify them every time, but you do need to re-verify them with the server administrators when they change.
If you're using sftp on Mac, Linux, or
WSL, you may see a message like this:
$ sftp -P 51022 XXXXXXX@activemft.research.cchmc.org
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
IT IS POSSIBLE THAT SOMEONE IS DOING SOMETHING NASTY!
Someone could be eavesdropping on you right now (man-in-the-middle attack)!
It is also possible that a host key has just been changed.
The fingerprint for the RSA key sent by the remote host is
SHA256:zcyKTFsVrw4Egzh6lb+MZV+7wLbynK7GSqW/uzc+5wM.
Please contact your system administrator.
Add correct host key in /users/usr0xy/.ssh/known_hosts to get rid of this message.
Offending RSA key in /users/usr0xy/.ssh/known_hosts:22
Host key for [activemft.research.cchmc.org]:51022 has changed and you have requested strict checking.
Host key verification failed.
Connection closed.In this case, use a text editor such as
nano
to remove the line indicated after the colon (line 22 in the above example)
from ~/.ssh/known_hosts and try again.
Hint: nano +22 ~/.ssh/known_hosts will
open the file directly at line 22, and Ctrl+K will delete that
line.
Important:
Upon your next connection attempt, you will be asked to re-verify the ActiveMFT server's host key fingerprint.
It's important that you do not skip this verification; make sure the fingerprint you are prompted with matches the one in the example above before proceeding. Contact us if it does not.
These fingerprint(s) are also listed on the "Downloading Results" page.
When using WinSCP, you'll see a
dialog box like this instead:
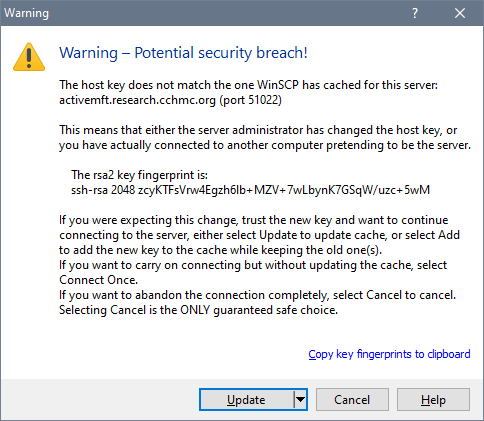
In this case—provided that the host key matches the one you see in the image—you can click the Update button to proceed.